Policy on Information Security
and Personal Information Security
Our services handle a wide range of financial data, and we believe constant enhancement of information management is essential, recognizing that appropriate management of information is a top priority to Money Forward as we sustain stable business activities.
To protect the information assets of users and of the Company from all threats, whether internal or external, intentional or accidental, the Company has established the “Basic Policy on Information Security (Security Policy)” and “Personal Information Protection Policy (Privacy Policy),” and is implementing appropriate defensive measures against risks including information leaks due to, among others, unauthorized access to its systems by a third party in bad faith to unlawfully acquire information.
In addition, the Company has established operational rules for information security management and internal rules for personal information protection, while also providing in-house training programs for officers and employees about the handling of personal information, in order to ensure that the rules that must be observed are fully understood and shared across the Company. Moreover, to effectively ensure full observation of said rules, the Company has made it a policy to take disciplinary action for a violation of said rules.
In March 2022, the Company established “Personal Data Statement,” declaring its principles for the handling of personal information, which includes not only data that could identify an individual, such as personal information and personal data as defined under the Act on the Protection of Personal Information, but also log information related to internet use, such as cookie data, IP addresses, terminal IDs and other identifier or location information of consumer users as well as their browsing history.
- ・Basic Policy on Information Security (Security Policy)
- ・Personal Information Protection Policy (Privacy Policy)
- ・Personal Data Statement
Information Security Implementation System
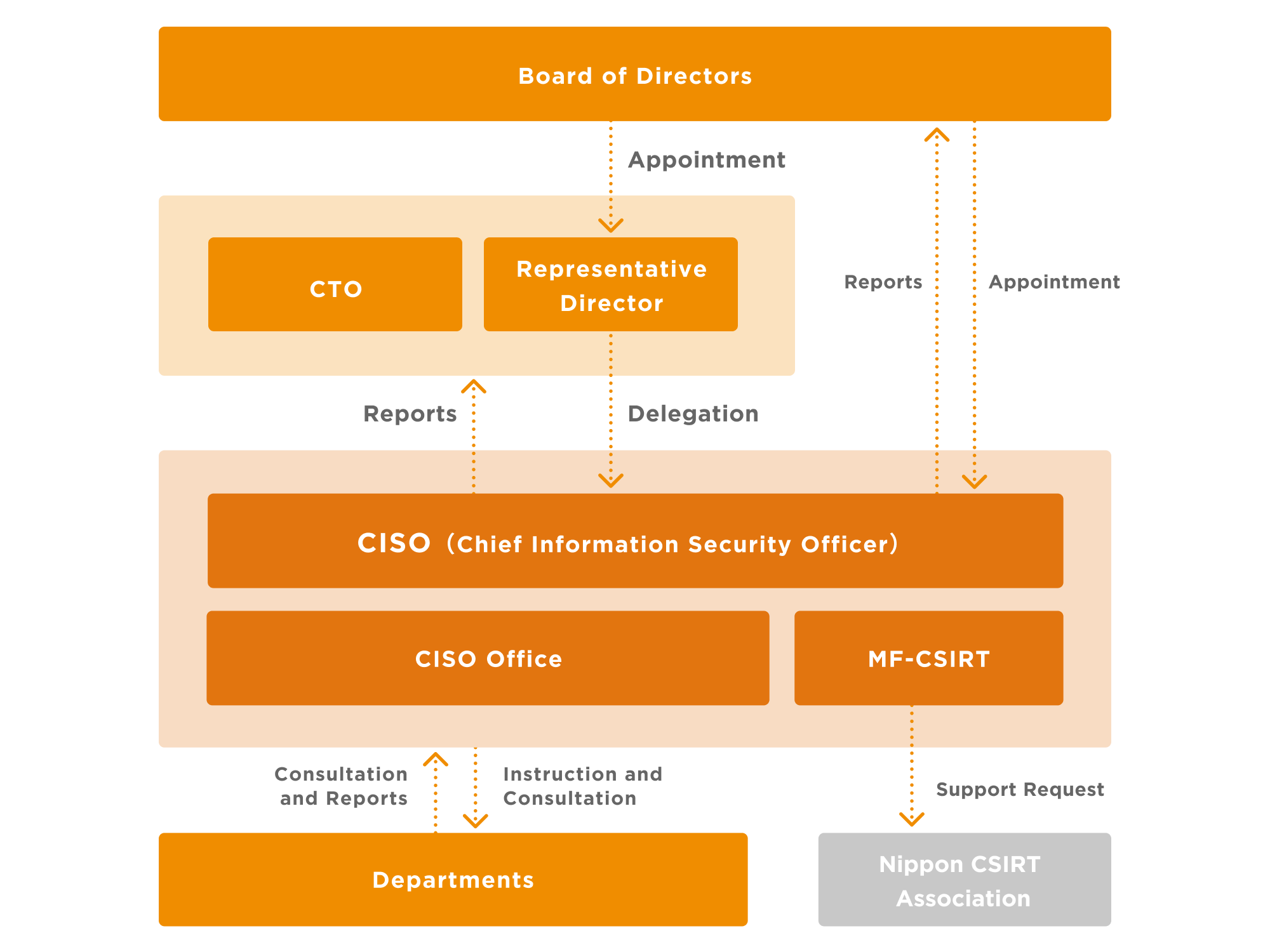
The Company has appointed a Group CISO (Chief Information Security Officer) as the person in charge of implementing information security operations with the CISO Office serving as the unit to lead initiatives to enhance information security. The Group CISO reports to the Representative Director, President and Group CEO and Group CTO (Chief Technology Officer) on the status of information security operations, including plans for security measures and their progress, risk assessment, and incident reports, on a monthly basis for evaluation and counsel as to the relevancy and effectiveness of information security operations, while also reporting to the Board of Directors on an annual summary of these monthly reports.
Major Initiatives related to Information Security and Personal Information Protection
Implementation of Security Training Programs
To ensure information security, the Company considers it essential that all who engage in the Company's operations appreciate the significance of the information handled by the Company and fully understand and abide by the relevant rules we must observe. From this perspective, the Company provides orientation programs for all employees regardless of the type of employment (including full-time, part-time, temporary and contract employees) to learn about information security, the handling of personal information, and IT tools used in the Company, in addition to information security training programs and online personal information protection training programs, offered when onboarding as well as regularly.
In addition, as an initiative to promote understanding and raise awareness about information security risk across the Company, the CISO Office communicates to the entire Company facts about information security incidents and near misses reported internally, as well as major information security accidents reported outside the Company, helping to prevent and avoid similar accidents and detect their early signs.
Protection of Information related to Aggregation Services
The Company offers services based on account aggregation technology that enables automatic linking of bank accounts of financial institutions and business corporations (aggregation services), and considers the protection of the information related to these services critically important. The Company only holds users' “log-in information” for affiliated services that they need to use to view such information as their bank statements and account balance, and does not hold any information that is used in affiliated services but is unnecessary for log-in, such as information for additional verification, random number tables, credit card numbers, and passwords for transactions.
Furthermore, the Company has adopted a 2048-bit SSL certificate, an encryption method of the highest standard, for data communications between the Company and affiliated service providers for aggregation services, encrypting and storing in separate servers the data that it holds and the verification information for affiliated services, while also restricting access to those data in order to ensure rigorous information security management and operations.
Prevention and Blocking of Unauthorized Access and Other Measures against Cyberattacks
The Company performs reviews during the development of systems and deploys a firewall for its systems for providing services and internal information systems to prevent unauthorized access from outside the Company. Company-provided PCs for officers and employees are equipped with antivirus software to block unauthorized access, such as a cyberattacks through internal devices by the use of malicious bots. The Company encrypts all major personal data, such as histories of deposits and withdrawals, while also applying encryption in data communication. By implementing these relevant measures, the Company works to enhance its security oversight capabilities.
In addition to these measures for preventing cyberattacks and information leaks, the Company has put in place a system that enables detecting and making emergency responses to extraordinary events in alliance with the SOC (Security Operation Center) by using EDR, so as to take action as soon as signs of hacking or information leaks are detected.
Assessment by External Information Security Experts
When undertaking new development projects or adding major improvements to existing services, the Company has external information security experts assess its application programs for vulnerability to ensure that there is no security issue. The Company also takes a penetration test, an assessment to see how difficult external professional engineers, familiar with cyberattacks, find it to hack the Company's systems and how long it takes and to determine the level of difficulty in breaking in.
Control of Access via Other Devices Than Company-Provided PCs
The Company provides officers and employees with PCs with relevant security management tools installed and prohibits them from using other devices than those Company-provided PCs when executing their duties. The Company's systems control major operational tools so that they cannot be accessed through devices other than Company-provided PCs.
Restriction of Access and Storing of Access Logs
The Company has completely separated networks for the environment for user services and for the environment for PCs of officers and employees, providing an environment where officers and employees are unable to access users' personal and other information on a fundamental level. When it is necessary to access users' personal and other information, employees can only handle it via VDI; provided that only a minimum number of employees, authorized by the Group CISO (Chief Information Security Officer), will be allowed to operate in this environment, with minimum authority given for each job. The operational history is recorded and regularly reviewed to assess the relevancy of data access. These operations are communicated across the Company to deter unnecessary access.
Implementation of Regular Checks and Audits
Those departments of the Company that handle personal information self-check the status of the handling of personal information within their own organizations and the CISO Office regularly reviews and analyzes operation logs containing personal information in the production environment. In addition, Internal Audit Office conducts operational audits covering the handling of information in general, while Corporate Auditors perform audits covering the handling of information in general.
Prevention of Information Leak by Retired Officers and Employees
The Company uses various SaaS services in its operations. If we performed the operations of creating log-in IDs, granting authority and deleting them for each of the systems for those SaaS services, it would complicate maintenance work and could, in the event of any omission, create the risk of retired officers or employees making unauthorized access. Accordingly, the Company has adopted SSO and automatic provisioning as well as integrated management for IDs of officers and employees to prevent any failure to delete IDs of retired officers and employees, which could lead to unauthorized access to the Company's systems.
In addition, the Company requires retiring officers and employees to submit a written secrecy pledge as a measure to prevent information leaks by retired officers and employees.
Engagement with Nippon CSIRT Association
The Company has engaged with the Nippon Computer Security Incident Response Team Association (Nippon CSIRT Association), collecting a range of information about incidents, vulnerabilities, and signs of cyberattacks, while also ensuring that if a security incident occurs and response efforts would go smoothly by seeking support, rather than by working alone, then the Company can ask member companies of Nippon CSIRT Association for assistance to implement swift and effective measures.
Acquisition of Information Security Certifications
To enhance information security and ensure that our customers can use our services safely, we are committed to obtaining various certifications. Below, we have listed the certifications our company has acquired.
PCI DSS Certification
PCI DSS (Payment Card Industry Data Security Standard) is a globally unified security framework for protecting credit card information, jointly developed by six international card brands: American Express, JCB, MasterCard, VISA, Discover and UnionPay.
・Certification Standard: PCI DSS Version 4.0
・Scope: Money Forward Pay for Business
・Certification Body: BSI Group Japan K.K.
ISO27001
ISO/IEC 27001:2022 (JIS Q 27001:2023) is an international standard for information security management systems (ISMS).
・Certification Registration No: IS 810207
・Scope of Certification: The providing of digital invoice services for supporting accounting business on SaaS service, and system design and construction, development, operation and maintenance of related systems
・Certification Standard: ISO/IEC 27001:2022, JIS Q 27001:2023
・Certification Body: BSI Group Japan K.K.

